Today I’m excited to announce that a16z is leading a $10.8M Series A financing of Keybase, a company that is trying to make the internet more secure by making public-key cryptography accessible to mainstream internet users. I’ll be joining Keybase’s board.
Almost every day we read about another major internet security breach. Recent examples include the Sony Pictures hack, in which confidential business emails were stolen and made public, and the Apple iCloud hack, in which private celebrity photos were stolen and made public.
Hackers are increasingly sophisticated, with the skills and resources to penetrate security systems that were developed mostly for a prior generation of threats. People are — quite justifiably — starting to question whether they can trust technology companies with their private information.
This is happening despite the fact that technology exists that can provide complete end-to-end security: public-key cryptography. Public-key cryptography was invented by mathematicians and computer scientists in the 1970s. It is hard to overstate the significance of this invention. As MIT computer science professor Scott Aaronson explains:
Even though cryptography has influenced human affairs for millennia, developments over the last thirty years have completely — yes, completely — changed our understanding of it. If you plotted when the basic mathematical discoveries in cryptography were made, you’d see a few in antiquity, maybe a few from the Middle Ages till the 1800's, one in the 1920's (the one-time pad), a few more around World War II, and then, after the birth of computational complexity theory in the 1970's, boom boom boom boom boom boom boom…
Using public-key cryptography, person A can send person B a message that nobody else in the world except person B can decrypt, even though persons A and B have never communicated before. Person A simply needs to know person B’s “public key” (a long number that can be listed in public) and use that to encrypt the message. Person B uses a “private key” (another long number that has a mathematical relationship to the public key and is kept private) to decrypt the m tessage.
Public-key cryptography means you don’t need to trust email providers, messaging companies, social networks, search engines, ISPs, cellular carriers, venture capitalists, tech startups, politicians, legal agreements, IT departments, and so on. You just need to trust math.
So why isn’t public-key cryptography widely used? It is, but in diluted form: various forms of cryptography are baked into almost every popular internet service. Yet the hacks and data breaches continue, mainly because the otherwise invulnerable cryptographic protocols are embedded within larger systems in which vulnerabilities are introduced by software bugs, employee mistakes, product design tradeoffs, legal constraints, management decisions, etc.
The ideal solution would be for users to adopt public-key cryptography themselves, in its pure, unadulterated form, without having to trust third-party service providers. Today, you’ll see this being done on occasion by more tech-savvy internet users. For example, here is Kashmir Hill, an investigative journalist for Fusion, publishing her public key on Twitter:

To send her an encrypted message, however, you’d have use software tools that are generally too complicated and cumbersome for mainstream internet users. As a result, public-key cryptography is mostly limited to a small circle of tech savvy security enthusiasts.
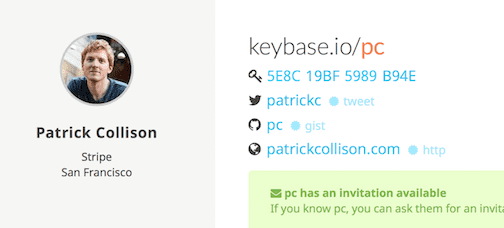
The idea behind Keybase is to make public-key cryptography accessible to everyday internet users. Keybase is, at its core, a database that connects people’s social media identities to their public cryptographic keys. For example, here’s the Keybase profile for Stripe co-founder Patrick Collison:
Each identity listed on his profile has been cryptographically verified to be owned by Patrick (other people can verify this for themselves by following the links on the page). So if you interact with Patrick as, say, patrickc on Twitter, you know the public key listed here is owned by the same person.
There are many things you can do with public-key cryptography besides sending messages. You can share files with individuals or with groups. You can verify that a file was created by the stated author and wasn’t altered (this use case is common with software developers who want to verify code they download doesn’t contain malware). In the future, you should also be able to use public-key cryptography to login to websites instead of having to remember passwords (this is already common behavior among developers who use cryptographic methods to login to servers)

A database by itself is useful to only the most tech savvy users. So Keybase is also building a set of applications to complement the database. These include native software clients for all the major platforms (iOS, Android, OS X, Linux, and Windows) that make it easy to do secure messaging and file sharing using the Keybase directory. Keybase will remain in invite-only private beta until the client software is ready.
A key design principle of Keybase is: you don’t have to trust Keybase. All the relevant software is open source and therefore independently auditable, fork-able, etc. The keybase directory is fully public and therefore also fully auditable, fork-able, etc. Everything you need to verify that you can trust the end-to-end cryptography is open and auditable. Keybase could get hacked or acquired or shut down and it wouldn’t affect the security of anything that uses Keybase. You don’t need to trust Keybase. You only need to trust math.
The founders of Keybase, Chris Coyne and Max Krohn, met at Harvard where they studied math and computer science and started their first company, SparkNotes. Max also got his PhD from MIT where he focused on security and file systems. Chris and Max and two other friends then founded OKCupid, where Chris and Max ran product and technology up until the company was acquired by Match.com in 2011. Chris and Max have both technical depth and consumer design savvy, an ideal combination for a project like Keybase.
Many of the best internet services were derived from ideas that came from Unix and the Unix-related academic and open-source communities:
Entrepreneurs have had considerable success adapting these amazing tools for mainstream use. Public-key cryptography has been cloistered within niche technical communities for too long. The time is right to bring it to the mainstream. We are thrilled to back the Keybase team on their mission to make that happen.
Keybase is hiring — more info here.