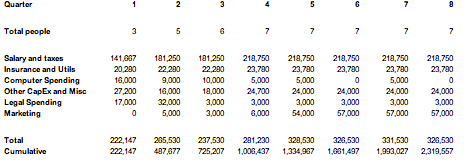It is widely believed that writing a business plan is a waste of time, because: 1) very few people will read it, and 2) you’ll end up changing it along the way. This is all mostly true.
However, before you commit yourself to working on a project for 5+ years, it’s prudent to think hard about what you are trying to build and some of the things that might go wrong. For many people, writing out a detailed business plan is the best way to enforce intellectual rigor.
My cofounders and I wrote a fairly long business plan for our first company, SiteAdvisor. We wrote it iteratively while getting lots of candid feedback from entrepreneurs, VCs, and industry executives (one of many reason you shouldn’t keep your idea secret).
I thought it might be useful to share our plan so I’ve embedded it below (at the time, we were temporarily calling the company InfiniTrust).
In retrospect, some things in the plan look prescient, some look naive, and some look downright goofy. But writing it was an extremely useful exercise. It made us think through issues we would have otherwise glossed over, and helped us stay focused when shiny new things could have led us astray.
As Eisenhower famously said: “plans are nothing, but planning is indispensable.”
***
InfiniTrust
January, 2005
InfiniTrust intends to create a new type of desktop security product that we call a “web reputation service.” The product will benefit users who value both unrestricted web access and security — primarily consumers and small and medium businesses. At the core of the product will be a database that classifies URLs, IP addresses, program downloads, ActiveX objects, and other “web entities” according to their degree of trustworthiness. There will also be a downloadable application that protects the desktop according to the security classifications in the core database. In addition, the company will provide plug-ins to firewalls, routers and web proxies (allowing for, among other things, the possibility of a fully managed outsourced web filtering service).
We see InfiniTrust as having a large addressable market. We believe the product will offer significant value to a large portion of the approximately 600M PCs in use today. Pricing for comparable products ranges from $2-$20 per PC per year depending on the product and channel. Since the marginal cost per customer will be extremely low (the main expense will be maintaining the database), we see the business as potentially having high gross margins.
Desktop security has become one of the top issues for individuals and organizations in the last few years and the problem has been only getting worse. We believe InfiniTrust represents a fundamentally new and important category of desktop security software, and if executed properly could become a leader in this emerging category much the same way Symantec and McAfee did in anti-virus or Brightmail and Postini did in anti-spam.
Problem
The data security industry has consistently ignored a large class of desktop security threats that they have considered to be “social engineering” or “user education issues” and therefore not addressable through their usual defense methods. Some examples are:
A user is confronted with an ActiveX prompt that asks him whether he trusts a company he has never heard of called Claria. The user knows that last time he saw a similar prompt on the ofoto.com website he said “No” the website failed to work properly, so this time he says “Yes,” enabling Claria’s Gator spyware software to take full control of his PC.
Typical industry response: The user should educate himself as to when to answer “Yes” or “No” to such prompts or should disable ActiveX altogether thereby rendering many popular websites dysfunctional.
A user receives a phishing email purporting to be from Citibank that is actually from a criminal in Uzbekistan trying to steal his credit card information. Citibank detects that the phishing attack has occurred but has no effective way to propagate defensive information to customers.
Typical industry response: The user should learn never to click on URLs in emails.
A user spends time browsing a music sharing website that exploits an unpatched hole in Internet Explorer to insert spyware on the user’s machine.
Typical industry response: The user should learn not to browse untrusted websites without modifying his browser security settings to restrict functionality like Javascript and ActiveX that enable most browser exploits.
A user downloads Grokster, a popular P2P file-sharing application. The user clicks “Agree” to Grokster’s 32-page End User License Agreement (EULA) without reading it carefully and therefore doesn’t realize that along with Grokster he is also downloading over a dozen different bundled spyware applications that will render his computer virtually unusable.
Typical industry response: The user should read all EULA’s before downloading software.
The data security industry has gotten very good at dealing with traditional security threats such as worms and viruses. These threats are characterized as 1) being unambiguously malicious and 2) having attack vectors that are primarily technical in nature. With more and more non-technical users having direct access to remote counterparties via email and the web, a new class of threats has emerged that are characterized as 1) having attack vectors that are primarily “social” in nature, and 2) not being clearly good or bad but instead involving tradeoffs on the part of the user.
Related to this trend toward “social” and “grey-area” threats has been the rise of economically motivated hacking. For example, spyware and phishing have quickly become big businesses. Claria (maker of Gator) generated about $90M in ‘03, primarily due to their distribution relationship with Kazaa. WhenU generated about $45M in revenue in ‘04, and there are literally dozens of other companies (e.g. 180Solutions, Direct Revenue) that are generating double digit millions in revenues. Estimates of losses due to phishing vary, but the numbers seem to be conservatively in the hundred of millions. In summary, there are literally billions of dollars generated every year by companies and criminals whose main “marketing” technique is exploiting the credulity and confusion of users.
Background on Spyware and Phishing
Spyware is an increasingly serious threat to desktop computer users. According to a recent study by Dell, 90% of computers are afflicted with spyware. Spyware help calls are the #1 issue handled by Dell customer support, accounting for 20% of all calls. Only 24% of computer users said they were knowledgeable about how to handle spyware.
Somewhat more conservatively, IDC estimates that 67% of computers have some form of spyware and that the market for anti-spyware software will grow from $47M in 2004 to $305M in 2008 (we think these estimates are very low—we know of specific anti-spyware companies that combined generated far more than $47M in revenues in 2004).
Phishing came almost out of nowhere in 2004 to become a major security threat. According to Gartner Group, 57M Americans have or think they have received phishing emails. Of those, 11% clicked on phishing links and 3% actually gave away sensitive information to attackers. The growth rates of phishing attacks have consistently been in the double and even triple digits month-over-month.
InfiniTrust Solution
The main features of the InfiniTrust product are as follows:
Site Protection: Adjusts the browser functionality dynamically according to the security rating of the website currently being browsed. For example, scripting calls to vulnerable ActiveX objects are disabled on untrusted websites but enabled on trusted sites. The point of this is to drastically reduce browser exploits that insert spyware and viruses, as well as eliminating “annoying” scripts such as pop ups, without reducing functionality of trusted sites.
Download Protection: Uses a whitelist approach to program downloads to warn or block the user before downloading an untrustworthy program (in an enterprise version,policy settings could be created to automatically block untrusted downloads without prompting).
Fraud Detection and Protection: Redirects the user to a warning page if he visits a fraudulent website such as a phishing landing page.
ActiveX Protection: Allows only whitelisted ActiveX objects to download or execute. Non-whitelisted objects are simply blocked, eliminating the need for user prompts.
Exploit Protection: Filters out browser scripting code associated with known exploits.
Ecommerce Protection: Warns the user about a poor security rating of a website before he enters his credit card information. In v2.0 will notify the user of summarized business-practice information about the site (using information from sources such as BizRate).
Privacy Protection (v2.0 only): Warns the user about the trustworthiness of a website before he submits personal information such as an email address. Also blocks cookies and other outbound transmissions of personal information to untrusted sites or ad networks.
In light of the recent high profile adoption of the Firefox browser (albeit mostly by the technical “elite” so far) it is interesting to note which of the Infinitrust features are “IE” specific and which provide a more general web security. Features #1, #4 and #5 are primarily for IE users. The other four features apply to users of all platforms and browsers.
In the case where InfiniTrust is being used as software installed on the desktop (as opposed to the firewall or web proxy API), it will either take automatic action or prompt the user with an easy-to-understand prompt depending on what’s most appropriate in case at hand. For example, when the user is browsing untrusted sites InfiniTrust will automatically restrict the browser’s functionality but when the user actively clicks on a downloadable program he will see a simple prompt explaining what, if any, malicious features the software contains.
In the case of the enterprise version the need for prompting will be obviated through policy settings created by the system administrator. Increasingly, many organizations are blocking all downloads and ActiveX controls altogether out of fear of getting spyware on the network. InfiniTrust will give them an alternative by providing them with 100% spyware prevention through its whitelist approach to ActiveX and downloads (in addition to browser exploit blocking).
Technology Plan
There are three main components to the InfiniTrust technology:
- Data collection/analysis. InfiniTrust will collect and analyze large amounts of disparate data sets to generate an “InfiniTrust Score” for every “web entity” (including downloadable programs, ActiveX objects, and website URLs/IPs). Input data sources will include:
Static analysis of web-crawled HTML and JavaScript.
Analyzed results of automated installations of downloadable software.
Data gathered from third party deals (e.g. IP intelligence services, phishing blacklist feeds, website and program popularity data)
Active and passive user feedback from users who opt-in to InfiniTrust’s product improvement program.
Information mined from publicly available sources (e.g., whois data, public blacklists)
Web site link analysis. As companies like Google has shown, if site X links to site Y, that is in some sense an endorsement by site X of site Y. Google uses this insight to rank the relevancy of sites, but it can also be applied to rank the trustworthiness of sites. If site X links to known untrusted site Y, then site X is more likely to be untrusted itself. Another way to put this idea is that the “dark alleys” of the web tend to be highly clustered in terms of link structure.
All of this will be processed to determine the degree of trust that someone should have when going to a particular website, downloading a particular piece of software, or engaging in some sort of commercial relationship with an online entity. Much of the true intellectual property of InfiniTrust will reside in the processes and tools for collecting and analyzing these input data sources.
2) Data servers. In order to balance load and decrease communication distances, the database will be replicated to a set of distributed data servers. Desktop clients will connect to these data servers in order to query for the security ratings of particular entities, or to periodically download software updates. The client software will include a caching mechanism to ensure that performance drag is negligible. Data servers will also receive back-channel information from users who opt-in to the product improvement program.
- Client agent. The client side agent takes action on behalf of the user or provides the user with easy-to-understand, relevant information. A client side agent consists of a core-agent that communicates with a data server, as well as an application-specific GUI agent that provides user-visible functionality. Most of these GUI agents will be web browser extensions, but they could also be built in to web proxies, or the underlying OS to protect non-traditional applications (e.g. software update tools) that make use of HTTP.
InfiniTrust plans to publish APIs and release an open source Linux/Firefox version of the client-side agents to facilitate partnerships with other software and equipment vendors. Access to the data feeds will be controlled with encrypted certificates.
In version 1.0, almost all of InfiniTrust’s data will be generated from public sources. As the user base and revenues grow, InfiniTrust plans to seek out additional data licensing deals. Examples could include phishing blacklists from anti-spam vendors and ecommerce data from companies like Bizrate. With a sizable user base, InfiniTrust could also become an important enforcement mechanism for “self-regulating” (and therefore mostly ineffective) programs and protocols like Trust-e and P3P. Down the road, we can also envision incorporating offshore manual labor into the data collection and analysis process.
Competition
Overview: We expect that in 2005-6 a lot of attention will be paid to problems like spyware and phishing. This is both good and bad for InfiniTrust. The risk is that other companies, especially large incumbents, either mitigate these threats significantly (less likely) or else create enough noise in the market to make the need for InfiniTrust less obvious (more likely). The good news is that InfiniTrust is specifically designed to complement existing security bundles. As pressure to differentiate security bundles increases, InfiniTrust could become an attractive add-on product or acquisition target. The historical pattern is that most of the innovation in consumer security has come from startups. For example, the software-based firewall was pioneered by ZoneLabs and anti-spyware was pioneered by companies like PestPatrol, Lavasoft and WebRoot.
Summary of existing anti-spyware technologies: Almost all of the anti-spyware products that currently exist are for removing spyware, not preventing it. It is widely believed that even the best anti-spyware removers achieve highly unsatisfactory success rates. For this reason, most experts recommend that users run multiple spyware removers (in addition, users are repeatedly instructed to be very careful where they browse, what they download, etc). This poor success rate is due mostly to the fact that once spyware takes control of a user’s PC and starts performing tricks like copying itself, changing the HOSTS file, disguising its signature etc, the technological problem of removing it becomes extremely difficult.
There are a few existing anti-spyware programs that claim to have spyware prevention features (e.g. SpywareBlaster, Microsoft’s AntiSpyware) but in fact just use highly inaccurate behavior-based techniques (similar to Intrusion Prevention Systems). In the near future, we expect security companies to develop blacklist-based preventative approaches to spyware. Blacklist approaches have a number of problems: 1) it is extremely difficult to keep spyware blacklists up-to-date and even a single mistake can render a PC unusable, 2) they don’t properly address the many sources of spyware that are “grey area” downloads. The problem of spyware is not nearly as black-and-white as problems like viruses and worms as most spyware comes through bundled adware where reasonable people can disagree about its maliciousness. InfiniTrust believes the best way for users to be both protected and have a satisfying browsing experience is to 1) whitelist trusted programs, 2) blacklist purely malicious programs, and 3) inform users about the trade offs (and alternatives) in the grey area cases in a very easy-to-understand way.
Summary of existing anti-phishing technologies: There are three primary methods for stopping phishing attacks today.
The first is simply for existing anti-spam companies to better filter phishing emails. Anti-spam technologies have achieved 95+% accuracy but are not perfect. Moreover, phishing emails can be particularly hard to detect as they often use zombie PC’s for delivery (thereby making IP-based blocking difficult) and contain content that looks very similar to legitimate content.
The second approach is to try to shut down the email delivery or landing page machines in the midst of an attack. A number of security companies do this on behalf of their customers who tend to be large financial institutions. We believe these methods are limited as they succeed only after the critical first few (~6) hours of phishing attacks. Moreover, from the desktop user’s perspective, even if these companies stop phishing attacks for, say, the top banks there are many other types of phishing attacks that these companies are not even trying to stop, such as the Tsunami-relief phishing attacks that were recently seen in large volumes.
Client-side solutions: These have the advantages of providing zero-hour defense and the ability to defend against fraud from all sources. There have been a handful of client-side solutions released recently from companies like Earthlink, Netcraft, WebRoot, and GeoTrust. InfiniTrust is a client-side solution that has distinct advantages over these client-side competitors. For one, because InfiniTrust will be collecting a nearly comprehensive database of existing websites, it can take a (partial) whitelist approach to phishing detection. The fact that a site clicked through to from an email doesn’t appear in InfiniTrust’s list of millions of legitimate websites is a strong indicator that the site is potentially fraudulent. It also goes beyond these other solutions insofar as it prevents non-email based attacks (such as keyloggers inserted through browser exploits) and also more “grey-area” fraud such as dubious but not outright fake ecommerce sites.
Notes on primary competitors:
Symantec: Generated $1.87B in revenue in 2004, 47% of which came from consumer products. Symantec has not yet released a spyware removal tool but is expected to in Q105. They have no client side phishing product today but will likely release one sometime this year.
McAfee: McAfee is the #2 consumer security software bundle. They currently have spyware detection but not removal. It is likely they will release spyware removal sometime this year.
ZoneLabs: ZoneLabs was acquired by Checkpoint in 2004 for approximately $250M. Their primary product is ZoneAlarm, a software-based firewall that had, as of 2004, at least 30M (free) users. They also sell a complete security bundle that has at least 1M paying subscribers. ZoneLabs built their business almost exclusively through a free downloadable version that became popular in the press and among technology enthusiasts.
Computer Associates: CA sells a traditional security bundle and recently added spyware removal tools through their acquisition of PestPatrol.
Trend Micro: Trend Micro has recently added spyware removal and has features they describe as anti-phishing (actually just an outgoing firewall that looks for personal info being sent from the PC).
Microsoft: Recently acquired an anti-spyware company (Giant) and an anti-virus company and is expected to release versions of each in Q105. There have been conflicting reports about whether they plan to charge for these services. Microsoft appears to see web-based security threats as a major headache. Firefox has supposedly gotten 10% of the browser market in just the past 6 months due in large part to users’ frustration with Internet Explorer security issues.
WebRoot: WebRoot is widely considered to have a very good spyware removal tool. Their rate of innovation has generally been very impressive. WebRoot generated $16M in revenues in Q404 alone, evidence that point solution security products can thrive in the consumer market. We had thought Webroot was likely to be acquired but last week announced a $108mm financing event.
Freeware: Lavasoft’s Ad Aware and Spybot S&D have been extremely popular free spyware removal tools. For example, Ad Aware consistently gets more than 2M downloads per week on download.com alone (there is also a paid version of Ad Aware that is rumored to have generated significant revenues for the company).
Websense: Websense is a $1B market cap company that is considered to be the leader in so-called web filtering technology. The primary focus of web filtering technology is to restrict corporate users from going to “bad topics” such as adult and gambling websites. They have recently added an optional, add-on security module that basically works by altogether blocking access to large blocks of websites associated with insecure activity (e.g. Kazaa.com). Websense severely restricts web access and is therefore only useful to (typically large) corporations that find such restrictions acceptable.
Would any of these competitors be likely to offer a product similar to InfiniTrust’s?
Today, InfiniTrust’s closest competitor in terms of the product itself is probably Websense. Websense has a database that in many ways is similar to InfiniTrust’s although much more focused on topics rather than security ratings. Websense has built a high growth business ($100M revs, $36M EBITDA, $1.2B market cap) focusing almost solely on larger enterprises. We see their entry into the consumer market as being unlikely but if they did enter it that could be a serious threat to InfiniTrust.
Anti-spyware vendors could also conceivably take an approach like InfiniTrust’s, although it would mean a fundamental change in how they go about building their technology and database. Right now their approaches are very similar to those of anti-virus technologies: they have databases of signatures they use to scan PC’s for existing infections (“parasites”), as opposed to InfiniTrust which has a database of all the “hosts” (websites, program downloads, ActiveX objects) that might carry those parasites. Determining the trustworthiness of hosts is simply a different technology problem than detecting and removing the parasites.
We see InfiniTrust as being fundamentally about providing secure, “unannoying” yet unrestricted web access, just as anti-spam companies try to provide secure, “unannoying” yet unrestricted email access. Spyware and phishing happen to be two important and growing security threats that have mostly web-based attack vectors. They are therefore important to InfiniTrust’s value proposition but that does not mean that InfiniTrust is just another anti-spyware or anti-phishing company.
Marketing Plan
The target market will be individuals and organizations that care about both security and unrestricted web browsing. InfiniTrust sees this as encompassing a large percentage of consumers and, to a somewhat lesser extent, small and medium businesses. Larger businesses tend to be satisfied with much “blunter” security instruments such as Websense that significantly restrict user web access.
InfiniTrust plans to offer a limited-functionality free version that can be downloaded directly from infinitrust.com and will also be distributed through channels. The current plan calls for the free version to offer the user basic defensive features but not have access to the full database. The free version will remind the user of its value by displaying periodic reminders of the specific dangers it has blocked or warned about. The paid version will likely start at $30 per year for consumers (discounted strategically for different target populations) and something in the range of $5-20 per seat per year for enterprises with an upfront licensing fee for the admin console.
Distribution Partnerships: ISPs, security software vendors, search engines, toolbar vendors and PC OEMs are natural distribution partners.
ISPs (especially dialup providers where consumer choice is greater) are increasingly trying to differentiate their services through security software they give to their customers. For example, security is the primary focus of recent television campaigns by AOL and Earthlink. Additionally, these companies incur significant costs handling customer support calls resulting from phishing and spyware. For example, Earthlink says that customer support costs them $120K per phishing attack. Deals with ISPs could either be pay per user (AOL pays McAfee $2 per user for anti-virus functionality alone which is generally considered a commodity) or unpaid distribution of the free product.
Large consumer security software vendors try to provide a single package that includes every existing category of security software. If InfiniTrust succeeds in convincing them that its product is complementary and useful, it could be seen as a critical addition to their bundles.
Toolbar vendors such as Google, Yahoo, Earthlink, MSN and Ebay have recently been incorporating security features for anti-phishing and anti-spyware. For example, Yahoo distributes PestPatrol and Earthlink distributes WebRoot. Earthlink built its own anti-phishing functionality. InfiniTrust’s data feed can make these toolbars significantly more powerful.
PC OEMs receive numerous calls from customers about browser security issues. As mentioned earlier, 20% of Dell’s customer service calls are about spyware. These companies are interested in not only reducing these costs but also differentiating their products. Many of these companies have shown a willingness to work with startups (e.g. Dell distributes Sunbelt’s anti-spyware solution, generating a significant portion of Sunbelt’s $30M in revenue).
A recent internal survey by InterActive Corp. of web search users showed that the safety of the sites they find was users’ #1 concern (cited by 77% of respondents as a “major concern”). As search engines are increasingly the “gatekeepers of the web,” it is natural for them to provide filtering and ranking based on security. At the simplest level, a partnership with a search engine could provide an InfiniTrust score next to search results in exchange for showing the InfiniTrust logo.
Financial institutions affected by phishing have expressed interest in distributing client-side anti-phishing solutions such as InfiniTrust’s as a way to offer protection their customers. For example, one recently developed anti-phishing toolbar, FraudEliminator, received business development cold calls from 3 major banks, Mastercard and Experian in just the past week despite having spent $0 on marketing.
PR: Desktop security was by far the #1 topic of discussion in the technology-related press in 2004. The fact that InfiniTrust solves growing, high-visibility problems like phishing and spyware as well as older problems such as browser exploits in a new way provides a great opportunity to leverage this attention. Initially, the technology press will be targeted, but the benefits of the product are widespread enough to attract mainstream media coverage.
Word of mouth: Most “unsophisticated” users choose their security software based on the recommendations of 1) the media, 2) their PC manufacturer or ISP, and 3) technologically sophisticated friends and family. Strategies for addressing 1) and 2) were discussed above. The strategy for addressing 3) is, among other things, to make the product and message amenable to technology enthusiasts. InfiniTrust’s client software will be mostly or completely open source, thereby showing goodwill toward the technology-enthusiast community and assuaging concerns that the client software might be in some way malicious (importantly, open sourcing the client will not jeopardize the business as the value lies primarily in the centralized database which will not be open). In addition, the company will build Firefox, Linux and Mac versions relatively early on and expose popular portions of the database to the public via search engines.
Paid marketing: In the past few years, online advertising channels such as search engines and banner ad networks have transformed the marketing possibilities for consumer software downloads and services. In particular, it is now possible to target customers by demographic and context far more efficiently than in the past. Moreover, startups are able to compete on a level playing field in keyword and banner auctions instead of having to, say, fight for shelf space in retail stores or suffer huge payouts to powerful distributors. Some consumer software products and services that have built interesting businesses primarily through web-based advertising and had recent successful exits include Gotomypc (acquired by Citrix for $237M), ZoneLabs (acquired by Checkpoint for $250M), Classmates.com (acquired by United Online for $100M), TripAdvisor (acquired by IAC for $250M), and Shopping.com ($750M market cap).
Risks.
Market risks:
Competitive offerings: Companies such as Symantec, McAfee and Microsoft could improve their products enough to substantially solve the same problems that InfiniTrust is trying to solve. These companies have superior brand recognition and distribution so even if they merely solve the same problems, say, 75% as well as InfiniTrust does, they will likely succeed in the marketplace.
Insufficient or inaccurate data: InfiniTrust may launch with a data set that is simply not sufficient to show real benefits to early adopters. It may be that deeper or broader data is required in order to cover an acceptable percentage of actual user browsing. Initial diligence, however, suggests this outcome to be unlikely because web browsing tends to be fairly highly concentrated. It has been shown, for example, that 50% of page views on the web are for the top 5000 websites, and the top 2000 downloads account for over 95% of total downloads.
Unwillingness to pay: While the InfiniTrust product may provide incremental value to users, there may not be a willingness to pay for it.
Lack of awareness: Despite attempts to build distribution partnerships and generate PR, customers may simply not hear about InfiniTrust. The cost of running a concerted advertising or paid inclusion program may simply be too high for a start up to muster.
Problems decrease for other reasons: Legal changes, software quality improvements or other external factors may lead to a reduction in the type of security problems that InfiniTrust solves, thereby reducing the need for the product.
Technical risks:
Data collection: The data required to make InfiniTrust work can be difficult to collect. Programs must be automatically installed, phishing attacks must be recognized, and web exploits must be discovered and analyzed. The company believes it has a solid plan for tackling these problems, but if it is wrong the product quality could suffer.
“Arms race”: Once attackers realize how InfiniTrust operates they may put more effort into hiding their spyware, phishing attacks, web exploits etc. This may result in a reduced data quality. Since most of the “hackers” InfiniTrust is targeting are economically motivated, the company believes this will only happen when the company is quite successful distributing its product. At that point the company expects to have the resources to fight back.
Budget
The company is raising $2.7M, which would allow for a 12 month product development plan plus an additional 12 months of marketing, business development, and product refinement. After the v1.0 product is built, the company would hire an additional team member to help with marketing and business development, and would also engage a PR firm and do online advertising to build market traction. A summary of the budget plan is below.